http://m14hackersworld.blogspot.com
Waffit (wafwoof) - Web Application Firewall Detection Tool | Backtrack 5 R3 | Tutorial
WAFW00F allows to identify and fingerprint WAF products protecting a website. This tool was written by Sandro Gauci && Wendel G. Henrique.
Features:-
Procedure
How to open it:-
To open it goto, Backtrack >> Information Gathering >> Web Application Analysis >> IDS IPS Identification >> waffit or you can also open it through Terminal by opening this directory cd /pentest/web/waffi.
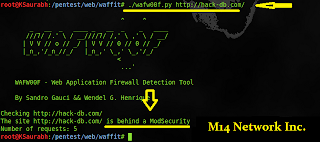
How to use it:-
To use it, run this command ./wafw00f.py
Verbose mode usage:-
To use it in verbose mode, run this command ./wafw00f.py -v .
There are few more options available for this tool, you can see it by running this command ./wafw00f.py -h.
I hope this article have helped you.
Waffit (wafwoof) - Web Application Firewall Detection Tool | Backtrack 5 R3 | Tutorial
WAFW00F allows to identify and fingerprint WAF products protecting a website. This tool was written by Sandro Gauci && Wendel G. Henrique.
Features:-
- This tool can only detect limited numbers of firewalls, listed below.
- Profense
- NetContinuum
- Barracuda
- HyperGuard
- BinarySec
- Teros
- F5 Trafficshield
- F5 ASM
- Airlock
- Citrix NetScaler
- ModSecurity
- DenyALL
- dotDefender
- webApp.secure
- BIG-IP
- URLScan
- WebKnight
- SecureIIS
- Imperva
Procedure
How to open it:-
To open it goto, Backtrack >> Information Gathering >> Web Application Analysis >> IDS IPS Identification >> waffit or you can also open it through Terminal by opening this directory cd /pentest/web/waffi.
How to use it:-
To use it, run this command ./wafw00f.py
Verbose mode usage:-
To use it in verbose mode, run this command ./wafw00f.py
There are few more options available for this tool, you can see it by running this command ./wafw00f.py -h.
I hope this article have helped you.

.PNG)

.PNG)
Post a Comment
M14 Network Inc. | Hassnain Arts